Is Skinning ALL Stardock Is About?
Or could it be they cater to wider interests?
Monday, August 15, 2005 by Zoomba | Discussion: Virtual Communities
Over time I started to explore the other sites and products from Stardock. I gave Object Desktop another spin and found it vastly improved since I had last visited the product set, and I found that there were other games for me to play. But to play them I needed a Dregnin subscription, so I got a discounted subscription since I was a GalCiv owner and got access to the rest of the Stardock games. While I was diving deep into the other products offered by Stardock, I stumbled on this site called JoeUser, yet another web log site. The difference here was the community focus and the style of articles written. It wasn't like LiveJournal where people whined and complained because their 8th grade boyfriend/girlfriend hadn't called in the past 2 hours and they missed them so much and how their parents just didn't understand how you two are deeply and truely in love and want to get married and have kids and you'll always be together and and and *gasps for air* Here on JU, it was (mostly) adult conversation. People wrote interesting things and debate/discussion often resulted.
From there I started fiddling with Stardock Central a bit more and noticed the IRC client, so I started popping into #Stardock and #GalCiv and would occassionally jump in on some conversation here or there. in #Stardock, mostly the topics revolved around skinning and the ObjectDesktop suite of tools. Sometimes it would wander and just be about silly fluff, but it usually came back to skinning. #GalCiv was pretty dead since a fair bit of time had passed since release of the game and interest had started to drop off. I frequented the channels off and on for about a year. It wasn't until GalCiv 2 was announced and then we started the JoeUser chat room that I became a more permenant fixture on the IRC server.
Why do I write all of this? Why do I recount my path of discovery as it relates to Stardock and its products and services? Well, because for some reason there are a lot of people out there who seem to think that ALL Stardock does is Windows Customization software and services. While I admit it's the lionshare of their business, it is not all they do. I have been chastised in #Stardock for having the audacity to start a conversation on anything that didn't directly relate to skinning. I've gotten put down for talking about GAMES and TECHNOLOGY before because it strayed too far from the sacred topic. People at WC lament regularly that content that may be relevant but originated outside of the sacred WC forums shouldn't be cross-posted as it is now, as if us unwashed masses are going to dirty the pure clean waters of their holy home. I just want to remind everyone that the skinner is not the only type of community member, it's not the only interest catered to by Brad & Co. Here's a quick list of some of the OTHER things Stardock does, for those of you who seem to have forgotten/been unaware of:
1. Game Development Company
Stardock has developed and released several top-notch games ranging from Lightweight Ninja, a Sonic The Hedgehog like sidescroller, to Galacitc Civilizations a turn based space strategy game to The Political Machine, a presidential campaign simulator. Up on the horizon they have Galactic Civilizations 2, a reinvention of the series in a damn good looking 3D engine as well as Society: The Game, a Real Time Strategy Massively Multiplayer Online Game. There are a lot of people out there who buy and play Stardock Games. With the addition of TotalGaming.Net, a new online game distribution channel, gaming is becoming a big pull to Stardock.
2. Online Communities
WinCustomize is probably the site everyone is the most familiar with since Win Customization is their biggest business right now, but they also have JoeUser, a great blog community that they just haven't started charging for yet. All of their sites attempt to foster community centered on the site topic, and they also attempt to share content across them when posted in relevant channels.
3. Office Productivity
Enter ThinkDesk, the latest tool offerings from Stardock. Right now there's only Multiplicity, which allows multiple computers to be managed from one keyboard and one mouse, but they've got other nifty goodies lined up to go. These programs are catering to a COMPLETELY different crowd than their previous offerings.
4. Unrelated but cool ventures...
Poweruser.TV comes to mind as a pretty cool and really different direction for Stardock to be going in. Here they're addressing all sorts of different topics that span everything they do and more. Games, customization, new technology etc. This is going to bring to the larger community, Power Users who might not have taken notice of Stardock in the past.
Now, gamers may explore and discover that they can also change the appearance and behavior of their computers, or skinners may find a new game they adore, or maybe people from either camp would find some insanely useful ThinkDesk tool that simplifies their real life work. Then maybe they would start posting thought-provoking aritcles on topics that interest them. It's a massive cross-pollination of thoughts and opinions, and it exposes us all here to something new that we might not have considered before. I know I dabble a lot more with ODNT, and plan on buying Multiplicity the second there's a Mac version and will probably poke around with the other tools when they become available. Stardock sucked me in with a single game, but now they have a customer that has bought a wide range of their products from all categories.
I just want you, the elitists amonst the WinCustomize community, to remember all of this next time you turn your nose up at anything that isn't connected to skinning. Remember that there are people out there in the Stardock network that didn't come here to tweak DesktopX, that didn't come here to get the latest ObjectBar skin and aren't interested/capable of making our own themes or whatnot. Remember that we, just like you, are customers of Stardock, we put in the cash just like you and we contribute in our own ways and in our own areas just like you do. We are no better and no worse than you are, so please cut the sneering, jeering and condescending tone you take with us. Stop acting all self-righteous when one of us writes a RELEVANT article in the areas of technology or the Internet and it gets crossposted to your sacred site. We get your stuff too all the time but you don't see us popping in on your threads saying "I don't think this belongs here on JU/GalCiv/Whatever site).
We're all part of a larger community, I hope you can learn to become better neighbors."
Windows Vista Preview (pre-Beta 1)
A general overview
Sunday, July 24, 2005 by Frogboy | Discussion: Windows Vista
 Very shortly Longhorn Beta 1 will be coming out. The current expected date is August 3, 2005. So what's in it? What can we expect? Microsoft was kind to inform a group of us what beta 1 would be like. Because of our NDA, I can only recap what is already known with a bit more detail. Once beta 1 ships, we'll be free to write more. And hopefully I'll be able to show some cool screenshots.
Very shortly Longhorn Beta 1 will be coming out. The current expected date is August 3, 2005. So what's in it? What can we expect? Microsoft was kind to inform a group of us what beta 1 would be like. Because of our NDA, I can only recap what is already known with a bit more detail. Once beta 1 ships, we'll be free to write more. And hopefully I'll be able to show some cool screenshots.
First off, as many already have heard, Longhorn has been christened "Windows Vista". It will probably come out in August 2006. In my view, Windows Vista has 3 goals:
1) Security. Microsoft wants to make sure Windows Vista is very secure. It will hopefully bring an end spy ware and malware and the like.
2) Developer Flexibility. A great deal of work in Windows Vista appears to be setting the stage for the future. Long ago, there was a second Microsoft OS code-named "Blackcomb" which was to be the follow-on to Longhorn. In my opinion, Longhorn is setting the stage for what comes next. It is doing this through the creation of several new, and more effective ways of creating content and software. For example, Avalon is a development platform that is designed to make it much easier to create visually exciting applications. It's a whole new presentation sub-system. Avalon applications are typically written in a new mark-up language called XAML. There is another mode called Avalon-Express applications which I think are particularly exciting -- Avalon apps can be run as part of a web page. Naturally, some Macintosh users will claim that this is like "Dashboard". And indeed there are similarities here. But Microsoft has been working on Avalon a lot longer than Apple was working on Dashboard. And Avalon Express applications are designed to be very secure from day 1. Another new development platform is called Indigo. It's .NET based and is designed to make it much easer to create network-based programs. And then there's the integration of RSS into the OS. Microsoft seems to believe that RSS is going to be a dominant way of making use of data in all kinds of interesting applications. We think the same thing. For example, when IE 7 starts coming close to release, we plan to make WinCustomize's skin galleries support RSS.
3) Polish. Microsoft had little more than a year to take Windows 2000 and turn it into Windows XP. This time, Microsoft has put a lot of effort into figuring out how to make Windows easier to use and have better "fit and finish" to it. Much of this is provided by the new user experience called Aero. And it really kicks ass. Early on, there were screenshots of concepts for Aero. They were bulky, ugly, and over-kill. Aero has come a long way though and Microsoft seems to be intent on making this version of Windows the most polished, cleanest, best OS they've made yet. We're not just talking about being pretty, which it is. But also being far more responsive to user input, booting up faster, better memory management.
When beta 1 comes out, bear in mind that the "good" stuff won't really show up until beta 2 Beta 1, I believe, is primarily designed to knock out compatibility bugs and put what's there through the ringer to make sure they've got a solid foundation in which to take care of the rest.
When you put all the pieces together, you have a pretty significant improvement over Windows XP. It should be a secure, fast, visually appealing OS that lends itself to new and innovative software development opportunities.
When Beta 1 is released, I can go into much more detail and with a lot more specifics. Stay tuned.
Related Articles:
Stardock & Windows Vista
A sneak preview..
Sunday, July 24, 2005 by Frogboy | Discussion: Windows Vista
 Windows Vista may be the most extensible version of Windows yet. With its rich new set of APIs that allow users to create unique applications quickly and that the interface has been moved away from GDI (the old drawing method) to a whole presentation system that makes use of 3D hardware acceleration, developers will be able to make Longhorn shine very so brightly.
Windows Vista may be the most extensible version of Windows yet. With its rich new set of APIs that allow users to create unique applications quickly and that the interface has been moved away from GDI (the old drawing method) to a whole presentation system that makes use of 3D hardware acceleration, developers will be able to make Longhorn shine very so brightly.
Stardock's goal on Windows Vista will be much the same as it was on Windows XP -- to enhance and expand the feature set of the OS. The difference this time is that Microsoft is giving us a lot more tools to play with.
 Object Desktop, Stardock's premier suite of desktop enhancement programs will be getting a host of new features in order to enhance the Windows Vista experience through customization and new abilities. At the same time, Stardock will continue to enhance its support for Windows XP users as well.
Object Desktop, Stardock's premier suite of desktop enhancement programs will be getting a host of new features in order to enhance the Windows Vista experience through customization and new abilities. At the same time, Stardock will continue to enhance its support for Windows XP users as well.
For example, WindowBlinds 5, which goes into beta this Fall, can support Aero-Glass type effects on Windows XP (see screenshot, that's Windows XP). DesktopX will take widget and gadget making to the next level on Windows Vista. DesktopX allows users to visually create mini-applications using an object-oriented interface. But under the covers, DesktopX creates XML and Javascript/VB Script files. In Windows Vista, our goal will be have DesktopX generate XAML code and hence, on a Avalon-enabled system to make use of everything Avalon has to offer. And on systems in which Avalon isn't, on, DesktopX can use its own internal DirectGUI engine.
Windows Vista, so far, looks to have more potential for enhancement and extension by third-parties than any Microsoft OS before it. It's built on a solid foundation and Microsoft really does seem to have taken the view of trying to create the OS as a platform as opposed to the OS as a application bundling opportunity (ala Apple). We'll keep you posted.
DesktopX 3.1 a winner!
Now get back to work!
Tuesday, July 19, 2005 by John Hamp | Discussion: DesktopX
It's restricted to just the desktop and most people seem to either use it to put a bunch of useless crap on their desktop. I mean really, do we need something to tell us what the weather is? Do I need another clock? Alternatively, other people seem to use it to make whacky looking desktops.
Not me. I use DesktopX to have a better Explorer experience than Explorer. I replace my common desktop icons with DesktopX objects. I've been using DesktopX regularly since the mid 1.x versions when it really started to solidify. I've never made a widget with it. I've stuck to enhancing my desktop objects with some Javascript to do things like tell me how much disk space is free or display the last time a site was updated as part of a website object's label. Nothing too fancy but USEFUL.
I wish Stardock could properly convey just how incredible DesktopX is. It is probably the single best desktop extender utility on the market today and has been for awhile if it's used properly. It pains me seeing Stardock chasing after the over-hyped, under-powered, over-blown Konfabulator cult when there's no evidence that people want widgets on any large scale. I think their "gadget" strategy is sound and maybe that'll start getting them to focus on what makes DesktopX special and that's eXtending the Desktop of Windows to have new functionality that behaves as if it's native.
Since Longhorn doesn't look to be doing mcuh for the Windows desktop, DesktopX is really our last best hope for users who want to have something more than just a bunch of useless icons on their desktops. Something other than a bunch of 'mini-applications' as well. DesktopX isn't a toy. It's the most productive enhancing tool out there when used correctly. Stardock, spread that message.
Fun with a Tablet PC
Almost The Dream, But Not there yet.
Thursday, July 14, 2005 by mormegil | Discussion: Laptops
Warning! Typos abound, or should I say hand writing mistakes, If you are eseyly offended Boy bat grammar and spelling, please move on to some one eleses Blog.
So I am writing this with a stylus on a tablet PC. I am amazed by How well The Hand writing Recognition seams to work. I am also amazed By How strange the errors are, when it dose not. I am not a very fast Typist. Nore a very gifted speller, and my penmanship seams To be equally sad. In Short, I should not Be allowed near a tablet PC.
Without, a keyboard, or a spellchecker, I am pretty much lost, But That is not what I am for in a tablet. I want it to Draw. ever since I saw a pre-tabet Computer called a Q De, way Back in 2000 at Comdex, I have Dremt of having one. My dream as always been to Have a kind of everlasting sketchbook, ant virtual Canvas, all the Freedom of carrying around a pat of paper, with all The power of all The best computer design programs. I often Thought how I would Sit outside ant Sketch Then be able to turn that sketch into a painting, or save it forever, or email it to a friend, (Yes I have once). well have been playing with This one for a few hours now ant, I can safely Say That My Incan is still a ways off.
My first-impressions were Leuc warm, but I have to admit that there is alot to be impressed by as I move on through The Learning curve. As a sketchbook it is not perfect. There is a good 1/4 inch cf pavalax Between were the tip of The pen It its The glass, cut were the "Ink" appears. I have Sean newer mobiles of tablets that have shrunk this to 1/8. But on This particular tablet (a Fujitsu stylistic) The gap is quite Large. There is even a wacom 21" Tablet That only has a gap of around 1/16. But Thats another bog entirely. what this gap means is That it dose not "feel" quite right. however, I did manage to find a enhanced Pen Driver from wacom. That dose make it Pressure sensitive, and allows for a much more natural feeling Than I would have thought.
As for painting, I am a bit Disappointed in The Computer itself. Sadly The Pentiums 3M, and 512megs of ram, are not Hacking it when it comes to Photoshop. Once I get a 8.511 x 11" image at 300 dpi, add in a few layers, and It comes to a crawl. but, It is still pretty cool, As long as I keep the files small.
the last Real problem is The size of The screen cut, resolution. The screen is only 11 ish inches, and running at 1024 x 768. which, is at the same time, to Small, and to large. the text is very small but, there is not enough screen real estate to fit The Photoshop Pallites. So the working area is very small.
So in Short I will keep dreaming of The perfect tablet PC. At the rate The technology is growing I will Be able to get my Dream one of these says.
P.S. This has taken about 10 times as Long to write, then it would have taken to type.
PSS. I Think this Tablet needs a skin. must ad that to my list.
How do you use Multiplicity?
Multiplying your computing power
Tuesday, July 12, 2005 by Frogboy | Discussion: Windows Software
 So what exactly is Multiplicity and why should you use it? Multiplicity is a program that allows users to take multiple computers in a given room and use them together as if they were one mega-computer. It's not quite "distributed" computing but in the hands of someone who knows what they're doing, it can come pretty darn close.
So what exactly is Multiplicity and why should you use it? Multiplicity is a program that allows users to take multiple computers in a given room and use them together as if they were one mega-computer. It's not quite "distributed" computing but in the hands of someone who knows what they're doing, it can come pretty darn close.
The idea behind Multiplicity is that each computer in the room still has a monitor hooked up to it. But only a single "master" computer needs to have a keyboard and mouse. The computers are connected together via a network connection (wireless, direct ethernet, firewire, whatever). Multiplicity can detect other computers that have it installed and allow the user to choose the physical location of the other computer (to the left or right of the master computer for example). When the user moves their mouse cursor onto a screen connected to another computer, the user is then controlling that computer. It's not remote control. The monitors are still connected to their respective computers. You're just using one keyboard and mouse to handle your various computers. Multiplicity then sets up a universal clipboard between the machines which helps them work together as one.
What makes Multiplicity special is its reliability and ease of setup and management. It's incredibly easy to set up and manage and has a lot of usability options that can help make people highly productive.
Multiplicity is used by all kinds of people. We've sold copies to test centers where a single person might want to be using several computers at once. We've sold it to IT departments where the IT administrator might want to clear off their desks of various keyboards and mice and use just one set to control the various computers under or on their desks. We've sold copies to graphics designers, 3D modelers, software developers, and power users. We even have a lot of people using it to help them play games.
So how is Multiplicity used? Here are some specific examples:
| Scenario 1: What do do with the old machine?
So you've got a new computer, but your older computer still has some life in it. Do you just let it collect dust? And what about getting all those files off of it? Multiplicity can solve that. Just get a cheap old monitor and hook it up to the old computer and use it right next to your new machine. As you need a file from your old computer, just right click on the file, choose copy, and then paste it onto your new machine's desktop. |
| Scenario 2: The laptop of tablet PC user
Your main desktop has the better mouse and keyboard on it. But you have a laptop (or tablet PC) that you use heavily. Multiplicity is very handy for this. You can use your main desktop machine's keyboard and mouse to control your laptop or tablet PC (if you have a tablet PC, Multiplicity is a must-have). |
| Scenario 3: The testing lab
Do you ever have to test something on multiple hardware configurations? Multiplicity lets you r clear your work area of excess keyboards and mice and lets you run those various computers from a single keyboard and mouse. If your desktop has more than one keyboard and mouse on it, you need Multiplicity. |
| Scenario 4: The Artist
If you use 3D Studio Max or Maya you should think about getting Multiplicity. Have one machine dedicated to rendering and another one that has your graphics editing package (Photoshop or whatever) and a third machine that you use that is your more casual office machine. You get the resources of all 3 machines, you can move graphics and such between all machines, etc. |
| Scenario 5: The software developer
Do you write software? Having one computer that is doing the actual debugging and coding and the other one that you use for everything else can be very handy. On a personal note, when writing Galactic Civilizations II it was very handy to be able to take screenshots on the development machine and then paste them into my Word document on the other machine to let me get ready for E3. But it also comes in handy because I never lose work due to "Bad things" happening to my other projects because debugging locked something up. I used to use SMP boxes and multi-monitor setups, never again. |
| Scenario 6: The Gamer
There's a bunch of scenarios for gamers. Whether that be the MMO player wanting to have two characters at once. Or the user who likes using Instant Messenger a lot but doesn't like getting interrupted while playing games. Or the gamer who wants to be able to surf the web for hints or whatever while they're playing but also doesn't want to give up any memory or CPU to other programs while playing. |
Multiplicity really does transform how you use your computers. Right now, as you read this, if you've got more than one keyboard and mouse on your desk, or you have a laptop and a desktop PC, you should definitely check out Multiplicity.
For those of you who have Multiplicity, let us know how you use it.
Multiplicity & Gaming
Playing two characters at once in World of Warcraft
Friday, July 8, 2005 by Frogboy | Discussion: PC Gaming
I admit it. I'm a bad man. It's not my fault though, I just don't have enough free time to be a good man. You see, I play World of Warcraft. It's a massively multiplayer on-line role playing game (MMORPG). In MMOs, you are, in theory, supposed to group up with other players to go on quests and such. I did this a lot when I was first got the game. I even have a guild with around 100 members. But as time has gone on, it's increasingly difficult to find people to go on quests with. So for me, World of Warcraft is pretty much like Blizzard's classic RPG, Diablo except in 3D, I play it single player.
The problem is, without other people, some of the quests are really hard. If only I had a reliable "friend" who could help me out. My son plays World of Warcraft on occasion. But he's not so much into questing as he is exploring and fishing. Sometimes we've played together -- I have two accounts, one for me and one for him. The second computer is only a few feet away from mine so we could play together.
And after dying that 3rd time trying to get through some cave, I would just look at that second computer. Just sitting there. What if I created an alternative character, like a priest or something to help out my first character so that when I am questing by myself, I can heal up myself just enough to get through. After all, I'm paying for two accounts and it's NOT a PvP server so it's not like it's harming anyone. The problem then is controlling both characters. Trying to juggle two keyboards and mice is tough.
That's where Multiplicity comes in. Using a network cable (or Firewire or a special USB cable that gives you an IP address) I hooked up both computers. I made my main machine the primary and my son's computer the secondary. Multiplicity then found the secondary machine right away and within minutes I was using both computers with one keyboard and mouse.
Only my primary computer needs the keyboard and mouse. When I move my mouse cursor off the monitor connected to my primary computer onto the monitor connected to the secondary computer, I'm now controlling it. The transition is perfect, that is, there's no lag at all. Now I was ready to fire up World of Warcraft and give it a try. I created an alternative character and made her ("Amanda") a priest. I then made a couple of macros that made it easier to have Amanda follow my main character around.
Within a few minutes, I was able to control both characters without any issue at all. I just whip the mouse over onto the other monitor to make some adjustments to Amanda and then back to my main monitor to be killing the monsters and what not. In instances where my guy would be getting overwhelmed, I just have Amanda cast a heal spell or a protection spell and off I go.
Now some people might say this isn't being fair. I say bull feathers to that. I'm paying for two accounts (me and my son's). If anything, I'm still at a disadvantage compared to the guy who has buddies helping them "power level" them. I'm still at a disadvantage to the guy who's guild buddies supply them with massive gold and equipment right away. And in terms of questing, having a party of 3 or 4 real people (and if I wanted to really get into this, I could use Multiplicity Pro and control 6 characters at once if I was really hard core) is still easier. But those of us who are more casual players or simply enjoy playing the game mostly as a single player experience, this is a great help.
Just as often I'm using Multiplicity so that while I'm traveling to some place in World of Warcraft I can move my mouse over to the other computer and be surfing the net, checking email, instant messaging, etc. all without having to worry that I'm slowing down my primary machine by using its memory and CPU.
Multiplicity is mostly used by companies and power users, but ironically, its ability to handle full screen games so smoothly makes it an excellent gamer's utility as well.
The evolution of TotalGaming.net
Indies of the world uniting
Thursday, July 7, 2005 by Frogboy | Discussion: PC Gaming
 ..A long time ago Stardock developed a game for OS/2 called Galactic Civilizations. It was published by a small company called "Advanced Idea Machines". Stardock never saw a penny of royalties from the retail release of the game. Learning from history, for Galactic Civilizations 2 on OS/2, Stardock decided to self-publish it. To get to retail, it worked with a distributor called Micro Central. Micro Central filed for bankruptcy and never paid a cent in royalties. Years later, in 2003, Stardock developed Galactic Civilizations for Windows and went with an "established" publisher called Strategy First. Strategy First soon after filed for bankruptcy without paying the bulk of its royalty payments. It remains Stardock's goal to one day get paid for retail purchases for a Galactic Civilizations game.
..A long time ago Stardock developed a game for OS/2 called Galactic Civilizations. It was published by a small company called "Advanced Idea Machines". Stardock never saw a penny of royalties from the retail release of the game. Learning from history, for Galactic Civilizations 2 on OS/2, Stardock decided to self-publish it. To get to retail, it worked with a distributor called Micro Central. Micro Central filed for bankruptcy and never paid a cent in royalties. Years later, in 2003, Stardock developed Galactic Civilizations for Windows and went with an "established" publisher called Strategy First. Strategy First soon after filed for bankruptcy without paying the bulk of its royalty payments. It remains Stardock's goal to one day get paid for retail purchases for a Galactic Civilizations game.
 But 2003 wasn't the same as 1993 (when the game was written for IBM's OS/2 operating system). Now we have the Internet in mass, Broadband access. And so Stardock's response was to create something called TotalGaming.net. The idea being that users would be able to buy and download Stardock's games. This system was up in its basic for when Galactic Civilizations I was released and thanks to it, there's still a Stardock's game team since nearly all the revenue Stardock collected from Galactic Civilizations was because of electronic purchases.
But 2003 wasn't the same as 1993 (when the game was written for IBM's OS/2 operating system). Now we have the Internet in mass, Broadband access. And so Stardock's response was to create something called TotalGaming.net. The idea being that users would be able to buy and download Stardock's games. This system was up in its basic for when Galactic Civilizations I was released and thanks to it, there's still a Stardock's game team since nearly all the revenue Stardock collected from Galactic Civilizations was because of electronic purchases.
Last year (2004), Stardock decided to expand TotalGaming.net and bring on other games. Nearly a dozen games were added to TotalGaming.net as of Spring 2005. The challenge going forward was how to bring on more games in a way that was fair to game developers. And that's where TotalGaming.net: Phase 2 comes in.
 With TotalGaming.net Phase 2, people can purchase games individually and then immediately download them. Because Stardock has been doing electronic distribution of software for years with its popular Object Desktop series of products, it has long since migrated away from digital rights management (DRM) techniques. Simply put, a user who pays $40 a video game expects to be able to download it and install it on their computer without any hassle. They expect to be able to put it on their laptop and be able to play the game on the plane. They expect to not have to worry about whether they installed it on "4" machines over the past 5 years sometime in the future. In short, they want to be treated as a customer and not as a potential thief.
With TotalGaming.net Phase 2, people can purchase games individually and then immediately download them. Because Stardock has been doing electronic distribution of software for years with its popular Object Desktop series of products, it has long since migrated away from digital rights management (DRM) techniques. Simply put, a user who pays $40 a video game expects to be able to download it and install it on their computer without any hassle. They expect to be able to put it on their laptop and be able to play the game on the plane. They expect to not have to worry about whether they installed it on "4" machines over the past 5 years sometime in the future. In short, they want to be treated as a customer and not as a potential thief.
Stardock's technology revolves around a technology called Secure Software Delivery (SSD) that it has developed over the past several years. It works on a basic assumption -- the piracy to really worry about is not about some guy giving their friend a copy of their game but rather someone putting a game up for download on a warez site or a peer to peer file sharing mechanism. Stardock Central, which is its practical application of SSD, works in a manner similar to iTunes -- users install the software via Stardock Central. But once it's actually installed, the user can use it whether they're connected to the Internet or not. They can play their game on the plane or install it to other machines in their home. It's designed to provide a balance between piracy resistance and customer convenience. And unlike most DRM schemes available, SSD has a proven 6 year track record with Stardock's own software. It's not any more secure than DRM, but it's a heck of a lot more convenience for gamers which, Stardock believes, is the key to success for wide distribution of electronic content.
In addition to being able to purchase games individually, they can also get a TotalGaming.net membership for $69.95 which provides 10 tokens. Essentially, users who think they'll be buying a lot of games have the ability to pre-purchase in exchange for a steep discount on the games. For instance, a user could pre-order Galactic Civilizations II for 5 tokens. Where the final game is expected to list for $49.95, TotalGaming.net members would effectively be paying $35 (half of the 10 tokens which cost $70 for all 10).
Armed with the new royalty system for game developers, Stardock has been able to attract a lot of independent game developers to put their games on TotalGaming.net. In fact, presently, the limit on getting new games is essentially a matter of how fast they can be reviewed and processed by Stardock's Brian Clair (formerly editor-in-chief of Avault.com). Moreover, TotalGaming.net is not going for quantity of games. While some emerging electronic distribution "stores" are boasting the sheer number of games they carry, TotalGaming.net games go through a very strict quality process (hence bringing in professional game reviewers such as Brian Clair to look at submissions).
Meanwhile, Stardock is also negotiating with large publishers who have libraries of excellent games that are just gathering dust due to not being available on retail shelves. Many of these games are just as good today as they were 2 or 3 years ago but have no real way of purchasing them.
Here are just a few of the new games on TotalGaming.net:
These are just a few of the games in there. We'll highlight more in the coming weeks. This just gives you a small taste of some of the cool stuff. Not only are there other awesome games in there from independent developers but Stardock has its own slew of new games that we'll be talking about more soon as well.
You can either purchase games individually or purchase a TotalGaming.net member ship. To learn more, go HERE.
Object Desktop in action
Learning how to super-charge Windows
Thursday, July 7, 2005 by Frogboy | Discussion: Beginners
 I have a lot of computers. It seems like I've always had more computers than one person should have. And each computer is different. I've got my development machine, I've got my casual office machine, I've got my laptop, and I've got my gaming machine. I even have a tablet PC.
I have a lot of computers. It seems like I've always had more computers than one person should have. And each computer is different. I've got my development machine, I've got my casual office machine, I've got my laptop, and I've got my gaming machine. I even have a tablet PC.
Each computer has different types of software on it and very different capabilities. And yet, by default, they all look and behave identically. Windows has always been a one-size fits all solution. Even the Tablet PC version of Windows is pretty much the same as every other version of Windows.
So what is a user to do? We all use our computers for different things so how can we easily custom tailor it to our needs? The answer: Object Desktop. Object Desktop has seen its popularity steadily increase over the years as users have found themselves wanting to tweak, modify, enhance, etc. the way Windows works.
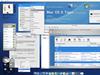
Many people see Object Desktop as a visual, cosmetic product for Windows. I.e. something that makes Windows "look cool". That's only a very small part of the story. In a screenshot or in a first impression, it's always that "cool" stuff. But as users get used to using it, they realize there's a lot more under the surface.
For this article, I'm going to stick with pretty basic stuff. Object Desktop gives you the power to really alter the way Windows works. But we don't want to go crazy just yet, let's go with some fairly straight forward stuff and go from there. I'm going to talk about my 3 main, non-specialized computers and how I use them. For the purposes of the screenshots, I'm doing them all on my development machine (the machine I'm on right now) to cut down on the time it would take to put all this stuff together for you. ![]()
All the programs I mention before come with Object Desktop which is only $49.95 and plus you get everything added to it for a year!
The Laptop
 I am probably the one guy in the world who runs his laptop at a relatively low resolution. My ThinkPad T42 laptop does up to 1440x1050 resolution but I tend to run it in 800x600 or 1024x768 when I'm doing email or browsing the net. And that's fine with Object Desktop which lets me transform the Windows UI into something optimized for low resolutions:
I am probably the one guy in the world who runs his laptop at a relatively low resolution. My ThinkPad T42 laptop does up to 1440x1050 resolution but I tend to run it in 800x600 or 1024x768 when I'm doing email or browsing the net. And that's fine with Object Desktop which lets me transform the Windows UI into something optimized for low resolutions:
![]() I use RightClick to have a new default right-click menu. I set it up to display my most frequently used programs along with a few other handy things on there such as my "Programs" menu. I have it set to automatically open when I hit the Windows key. Sometimes I tell it to hide my Start bar to get a bit of extra space. But I go back and forth on that depending on what I'm doing.
I use RightClick to have a new default right-click menu. I set it up to display my most frequently used programs along with a few other handy things on there such as my "Programs" menu. I have it set to automatically open when I hit the Windows key. Sometimes I tell it to hide my Start bar to get a bit of extra space. But I go back and forth on that depending on what I'm doing.
![]() I also turn on IconX. That's because I sometimes will have my icons be only 24x24 on the desktop. That's smaller than the default icons and IconX can scale my icons much better than Windows can. The new version of IconX lets me specify labels so I can have nice big labels still for the icons. These days, icons are pretty useless for individual things it seems like (IMO) and labels are much more useful.
I also turn on IconX. That's because I sometimes will have my icons be only 24x24 on the desktop. That's smaller than the default icons and IconX can scale my icons much better than Windows can. The new version of IconX lets me specify labels so I can have nice big labels still for the icons. These days, icons are pretty useless for individual things it seems like (IMO) and labels are much more useful.
![]() When I'm using my Start bar, I use the new Stardock Virtual Desktops. It's faster than other virtual desktops I've used and makes it easy to get more screen space when I need to.
When I'm using my Start bar, I use the new Stardock Virtual Desktops. It's faster than other virtual desktops I've used and makes it easy to get more screen space when I need to.
![]() I also use the Silica Media Player widget. And I admit, I mainly use it to control iTunes at this point. I have it set to come up when I hit the F12 key so I can quickly zip through songs.
I also use the Silica Media Player widget. And I admit, I mainly use it to control iTunes at this point. I have it set to come up when I hit the F12 key so I can quickly zip through songs.
![]() Keyboard LaunchPad is really crucial on my laptop. The reason is that, especially when traveling on the plane, I don't have much room for a mouse and while I like IBM's Trackpoint technology, it gets a bit old navigating to particular programs. So what I do is I have my common programs tied to a series of hot-keys. I am hoping that the next version will let me control iTunes directly from it (not that I don't like my media player widget but I pretty much just want to control things via the keyboard at that point).
Keyboard LaunchPad is really crucial on my laptop. The reason is that, especially when traveling on the plane, I don't have much room for a mouse and while I like IBM's Trackpoint technology, it gets a bit old navigating to particular programs. So what I do is I have my common programs tied to a series of hot-keys. I am hoping that the next version will let me control iTunes directly from it (not that I don't like my media player widget but I pretty much just want to control things via the keyboard at that point).
![]() Last but not least is WindowBlinds. I use it to run some minimalist skin. It changes my entire Windows GUI to have a nice, simple looking skin. But it is also important because I can set it so that when I right-click on a title bar it minimized the window.
Last but not least is WindowBlinds. I use it to run some minimalist skin. It changes my entire Windows GUI to have a nice, simple looking skin. But it is also important because I can set it so that when I right-click on a title bar it minimized the window.
What I've used Object Desktop to do is to get the most out of my limited screen space. I want to be able to get to things very quickly and I'm not very concerned about what is on the desktop or what is pretty.
The Development Machine
 My development machine is typically running at 1600x1200. So my screenshot isn't really reflective of just what I tend to have on it. My development machine is where I do everything from write code for Galactic Civilizations to creating new skins, objects, scripts, etc.
My development machine is typically running at 1600x1200. So my screenshot isn't really reflective of just what I tend to have on it. My development machine is where I do everything from write code for Galactic Civilizations to creating new skins, objects, scripts, etc.
![]() First off, I use DesktopX, as an environment here. The whole "widget" thing has kind of created some confusion on what exactly DesktopX is for. DesktopX is a desktop environment. It lets you have real objects on your desktop. In this case, what I do is import widgets and other content onto my desktop. Widgets are great but each widget is a mini-program. Imported content, by contrast, use very little memory because DesktopX itself takes care of running them. So I tend to import my To-Do list, various RSS feeds, stock-tickers, sticky-notes, etc.
First off, I use DesktopX, as an environment here. The whole "widget" thing has kind of created some confusion on what exactly DesktopX is for. DesktopX is a desktop environment. It lets you have real objects on your desktop. In this case, what I do is import widgets and other content onto my desktop. Widgets are great but each widget is a mini-program. Imported content, by contrast, use very little memory because DesktopX itself takes care of running them. So I tend to import my To-Do list, various RSS feeds, stock-tickers, sticky-notes, etc.
I also have a bunch of custom objects that I can't take screenshots of that display the status of our various databases and stores, and recent bug entries into our bug database. We created these with DesktopX too.
![]() The Silica Calendar widget is one I always run. So often I just don't remember which day of the week something will be and while I can double click on the clock in the Start bar, it's a lot quicker to hit F12 to bring up the calandar.
The Silica Calendar widget is one I always run. So often I just don't remember which day of the week something will be and while I can double click on the clock in the Start bar, it's a lot quicker to hit F12 to bring up the calandar.
![]() Not that my code ever has memory leaks but I also make heavy use of the Silica Memory meter widget. So I can keep track of my overall memory use to see if something is leaking.
Not that my code ever has memory leaks but I also make heavy use of the Silica Memory meter widget. So I can keep track of my overall memory use to see if something is leaking.
![]() I also run RightClick on this desktop. Except on this machine, I have all my development tools right off the main menu.
I also run RightClick on this desktop. Except on this machine, I have all my development tools right off the main menu.
![]() I use Keyboard LaunchPad to do only two things really -- first, I have Visual Studio and its corresponding tools all assigned to a single hot key. So when I hit Ctrl-Shift-D on my system it loads up several programs at once. And secondly, I have Ctrl-Alt-1 through 6 specified to load up a bunch of web pages I often go to.
I use Keyboard LaunchPad to do only two things really -- first, I have Visual Studio and its corresponding tools all assigned to a single hot key. So when I hit Ctrl-Shift-D on my system it loads up several programs at once. And secondly, I have Ctrl-Alt-1 through 6 specified to load up a bunch of web pages I often go to.
![]() I use WindowBlinds primarily for cosmetics on this machine. I just want my GUI that I'm staring at all day to look cool.
I use WindowBlinds primarily for cosmetics on this machine. I just want my GUI that I'm staring at all day to look cool.
![]() Ditto with IconPackager. IconPackager lets me change all my Windows icons to something that looks cool.
Ditto with IconPackager. IconPackager lets me change all my Windows icons to something that looks cool.
My overall strategy here is that I turn my desktop into a headline news reader with lots of objects on here that gives me all kinds of info. I also keep track of my resources and schedule. But I also care about how it looks, I want it to be nice looking as well.
The Gaming Rig
 The gaming rig is my play machine. It's ridiculously powerful for game playing. I do quite a bit of work on here too as I end up doing a lot of web work and such on this machine. But mostly I'm playing games on it. It has a really good video sub-system (right now an ATI X800 on it) so I tend to be able to turn on a lot more eye candy than I might otherwise use. I also tend to change the way it looks a lot since my tastes vary quite a bit.
The gaming rig is my play machine. It's ridiculously powerful for game playing. I do quite a bit of work on here too as I end up doing a lot of web work and such on this machine. But mostly I'm playing games on it. It has a really good video sub-system (right now an ATI X800 on it) so I tend to be able to turn on a lot more eye candy than I might otherwise use. I also tend to change the way it looks a lot since my tastes vary quite a bit.
![]() First off, I use WindowFX very heavily here. WindowFX lets me add shadows to my windows. It also has a feature that lets me scale my windows. This is incredibly cool. Basically I can assign it so that when I hold the SHIFT button when I click on the minimize button, it will turn the window into a scaled window (See the screenshot for an example). I can even interact with the window even when it's scaled which is quite useful if I am doing IM in a scaled window.
First off, I use WindowFX very heavily here. WindowFX lets me add shadows to my windows. It also has a feature that lets me scale my windows. This is incredibly cool. Basically I can assign it so that when I hold the SHIFT button when I click on the minimize button, it will turn the window into a scaled window (See the screenshot for an example). I can even interact with the window even when it's scaled which is quite useful if I am doing IM in a scaled window.
![]() Again, I have WindowBlinds here and I tend to have various kinds of skins running. I don't stick with anything very long. I will often just pick whatever is the currently featured skin.
Again, I have WindowBlinds here and I tend to have various kinds of skins running. I don't stick with anything very long. I will often just pick whatever is the currently featured skin.
![]() Same with IconPackager. I have it change all my icons to something cool.
Same with IconPackager. I have it change all my icons to something cool.
![]() IconX is where I really have some fun. First, I set my default icon size to 64x64. So they're very large. Secondly, I have the mouse over size be 128x128 and I have it animate to that size so that grow on mouse over. Some icons in particular I change to use a PNG file. I am hoping that a future version of IconX will let us set individual icons to have their own unique size but I'm not sure how the UI would be done for that.
IconX is where I really have some fun. First, I set my default icon size to 64x64. So they're very large. Secondly, I have the mouse over size be 128x128 and I have it animate to that size so that grow on mouse over. Some icons in particular I change to use a PNG file. I am hoping that a future version of IconX will let us set individual icons to have their own unique size but I'm not sure how the UI would be done for that.
![]() The Silica Picture Frame is very nice to have. Remember, this is a home machine, so I will tend to have a lot of company over from time to time. So I have the Silica Picture Frame widget cycle through the latest family photos. I can resize it to be any size I want so if I have a lot of guests over, I'll make it full screen.
The Silica Picture Frame is very nice to have. Remember, this is a home machine, so I will tend to have a lot of company over from time to time. So I have the Silica Picture Frame widget cycle through the latest family photos. I can resize it to be any size I want so if I have a lot of guests over, I'll make it full screen.
![]() The Silica Drive Meter. I use this because this is also the machine I take my home movies and turn them into DVDs. As you can imagine, the work files for this can get pretty huge so I tend to want to keep real-time track of my disk space as some of the cryptic programs I use for messing with video files don't bother to check to see if there's enough space to do what they're going to do before hand.
The Silica Drive Meter. I use this because this is also the machine I take my home movies and turn them into DVDs. As you can imagine, the work files for this can get pretty huge so I tend to want to keep real-time track of my disk space as some of the cryptic programs I use for messing with video files don't bother to check to see if there's enough space to do what they're going to do before hand.
![]() I don't use the Stock monitor widget as much as I used to. I don't have a lot of stocks but last Winter before I sold some stock I was using this quite a bit. I suspect others would find this useful too.
I don't use the Stock monitor widget as much as I used to. I don't have a lot of stocks but last Winter before I sold some stock I was using this quite a bit. I suspect others would find this useful too.
![]() Enhanced File Dialog is still in beta on Object Desktop but I find it incredibly useful. Basically it extends your existing Windows File Load/Save dialog to let you have additional functionality (resizable, add new places on the left side, have some quick launch buttons in there, etc.). A lot of the graphics programs I use don't seem to remember where I want to load images from or where I want to save images to and so being able to press a button to get back to where I want to go is a life saver. When this program is completed, I'll put it onto my other machines but the other production machines don't tend to run beta software which is why I only have it on this machine.
Enhanced File Dialog is still in beta on Object Desktop but I find it incredibly useful. Basically it extends your existing Windows File Load/Save dialog to let you have additional functionality (resizable, add new places on the left side, have some quick launch buttons in there, etc.). A lot of the graphics programs I use don't seem to remember where I want to load images from or where I want to save images to and so being able to press a button to get back to where I want to go is a life saver. When this program is completed, I'll put it onto my other machines but the other production machines don't tend to run beta software which is why I only have it on this machine.
The tip of the iceberg
Everything mentioned above comes with Object Desktop -- today. And believe it or not, I've barely scratched the surface. Object Desktop is probably one of the best software deals on the planet. It comes with everything you need to turbo-charge your Windows desktop to work however you want it to work. We haven't even gone into talking about ObjectBar or SkinStudio or IconDeveloper or how you create things with DesktopX. And we haven't touched on how you can use these programs to really change the way Windows looks & feels. I'll leave that for another time.
| Object Desktop | |||||||||||||||||
| |||||||||||||||||
Some other screenshots:
Loading a desktop with DesktopX (Newbies #15)
Cordelia's Corner for the Complete No0b #15
Thursday, July 7, 2005 by Cordelia | Discussion: Tutorials
Today's topic is loading a DesktopX 3.0 desktop. A DesktopX desktop is basically a snapshot of your desktop. It can be a desktop you've arranged with all of the widgets and objects you like displayed in a pleasing manner (or a displeasing manner, if you have a taste for suffering. Who am I to judge?).
It might also be something that has been set up for "fun" - I'll have to look up this "fun" word when I'm done here. Perhaps someone could provide me with a tutorial on "fun"?
And finally, a desktop might be a secure environment that restricts the user to a limited number of functions. Why would anyone want to do this, you ask? Well, what if you have small children and want to restrict their access to certain programs/folders on the computer. Admittedly, many 5 year olds know more about computers than I do, but it is still possible to restrict them.
|
Let's see some examples of this. Here is a screenshot of my current desktop.
| |
|
Now I open DesktopX and click on Load Desktop...
| |
|
There are 2 desktops that currently come with DesktopX 3.0. The first one is a game called "Keepie Ups" and it looks like this (click on thumbnail for a larger view). If I click on that soccer ball, the game tallies how long I can keep it in the air. You can see my pathetic score in the upper right and left corner of the screen. I don't feel bad, though - I've always sucked at any sport other than self-loathing or running away. | |
|
The next desktop is the "Guest" desktop. Have family coming over for a visit? Will they all be clamoring to use your computer? Load this desktop and restrict their access to your files. One button takes them to the Internet, and the other can be set up to take them to a program they can use - perhaps "Word". Simply right-click on the "My Program" icon and set the link to go to the program you want. |
Notice that any widgets or programs you have running when you set the desktop will remain active and visible after you set the desktop.
This desktop is not secure. This desktop would be perfect for my mother (whom I love very much, but who is a technophobe), however most small children will have this desktop unloaded in a matter of seconds. Truly secure desktops can be created with DesktopX Enterprise Edition, but that is well beyond the scope of this article.
And that, my friends, is all there is to loading an already made desktop. Making your own is a whole other article. Probably the next one ![]() .
.
If you don't have DesktopX 3.0 you can get it here.
https://www.stardock.com/products/desktopx/dx-faq.asp
This link will take you to the FAQ page for DesktopX. It's quite possible that I am leaving a lot of questions unanswered in this tutorial, and it's not because I don't like you. (I do, believe me.). It's a very complicated program, and it seems to me that if you can imagine it, you can create it with DesktopX. My little tutorials are just for beginners, no0bies, greenhorns...etc.
Check out the other Newbie Tutorials here: #1: Intro., #2: WindowBlinds, Part 1, #3: WindowBlinds, Part 2, #4: Screenshots, #5: IconPackager, #6: Wallpaper Basics; #7: Logon Studio; #8: CursorXP; #9: BootSkin; #10: RightClick; #12: WindowBlinds Advanced; #13: DesktopX 3.0: Loading Widgets; #14: Loading Objects with DesktopX
My Desktop:
Skin: Encoded by PixelPirate (It's new, and it's awesome)
Cursors: Encoded by PixelPirate (Keeping with the theme)
Wall: Simplicity by Nerio (Ok, I've used it before, but I can't help it: it's good and it just goes with a lot of stuff!)
Icons: Icon-A-Day by mormegil (was there any question what I'd be running?)